Sensitive info leakage via .gitignore
Hello everyone, it’s Wareeq Shile here with a short and sweet discovery I made a while back. In this post, I will discuss an instance of sensitive information leakage through a misconfigured /.gitignore file. For the sake of the client’s privacy, I will keep the target anonymous. First, let’s discuss the basics of Git and how a misconfiguration can lead to a security vulnerability.
BACKGROUND
For those unfamiliar, Git is a version control system that allows developers to track changes made to their project and push those changes to a repository.
When working with Git, developers can use the combination of the “git add” and “git commit” commands to save the current state of their project. However, sometimes certain files or directories may contain sensitive data or may not be necessary in the repository. In these cases, developers can use a .gitignore file to prevent Git from tracking changes to those specific files or directories. However, if the .gitignore file is not properly protected, it can lead to significant issues for a company or organization. It is important to ensure that this file is properly configured and protected to avoid any potential data leaks.
DECTECTION
To detect this vulnerability, you can use a file and directory brute force tool like dirsearch with a comprehensive wordlist. Alternatively, if automated tools are not allowed, you can manually browse to URLs like https://example.com/.gitignore and check for other Git paths like .git/config, .git/HEAD, .git/logs/HEAD, and .git/index.
While testing a web application, I discovered that the .gitignore file was publicly accessible. This file, which is typically used to prevent certain files and directories from being tracked and pushed to a Git repository, contained sensitive information such as login credentials and other sensitive data. This misconfiguration posed a significant security risk, as it allowed anyone to access sensitive information that should have been kept private. It is important for developers to ensure that the .gitignore file is properly protected and not publicly accessible to prevent similar security issues.
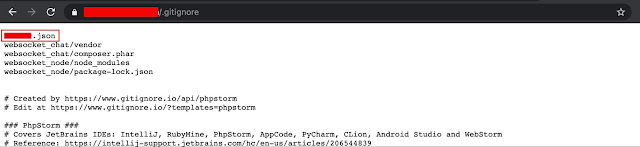
Upon further examination, I discovered a JSON file within the directories containing sensitive information such as MySQL database login credentials. This lack of proper protection could have serious consequences for the company or organization using this repository.
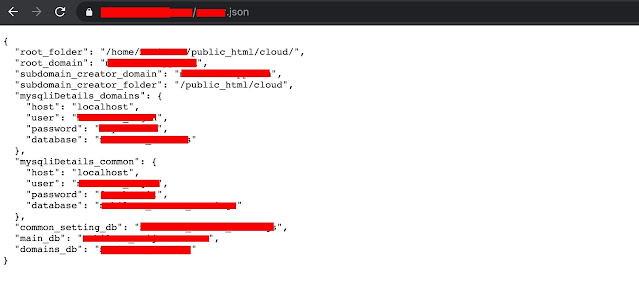
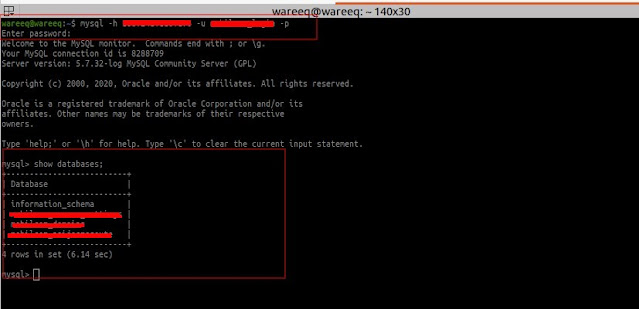
Mysql remote connection was enabled and I was able to login into the database using these credentials.
REMEDIATION
To fix this issue, the file permissions for the .gitignore file need to be revised to ensure that it is not publicly accessible. This can be done by setting the permissions to allow access only to authorized users, or by restricting access to the file altogether. Additionally, it is important to ensure that all sensitive information, such as database login credentials, is stored in a secure location and is not included in the .gitignore file or any other publicly accessible location.
CONCLUSION
Oftentimes, application content will exist that is unknowingly accessible, which may then results in a negative impact on the security of the system or organization. For reasons like this, I encourage spending more time enumerating and understanding the target.